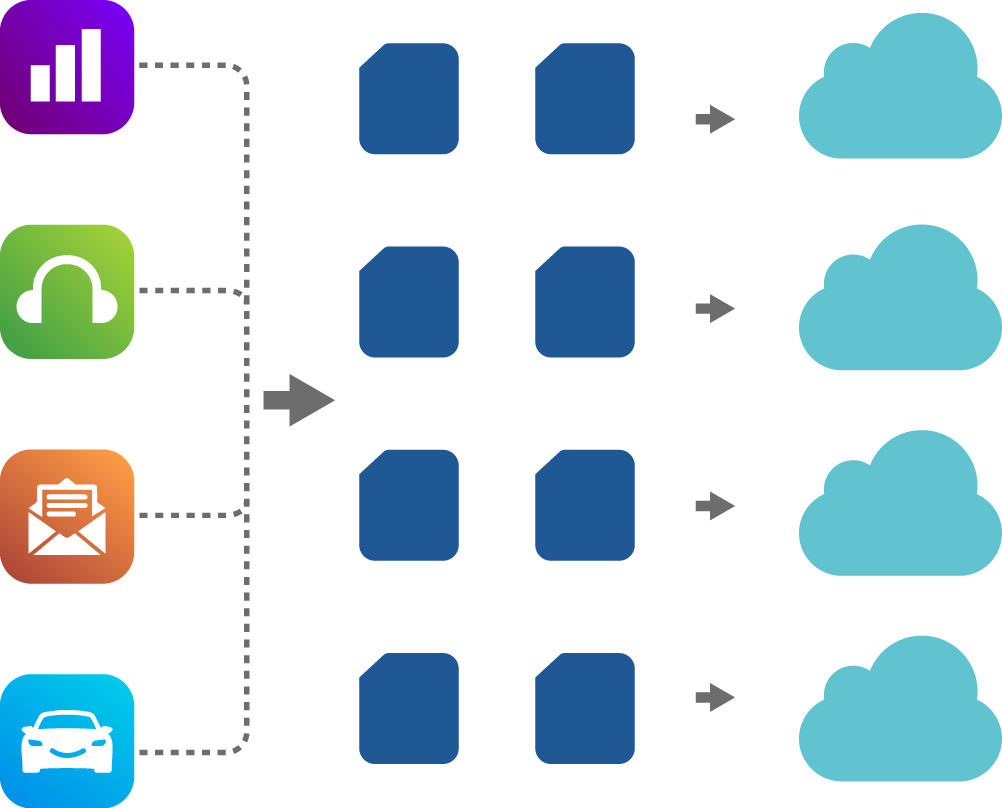
Storing data in encoded pieces has fancy names such as "Information Dispersal Algorithm", "Shamir's Secret Sharing", "Non-Systemic Erasure Code". This concept has been in use at large enterprises, web scale companies, and high-performance compute (HPC) environments.
Many of the classic industry algorithms and open source implementations relies on Galois Field arithmetic for encoding data into pieces. This involves heavy computing resources. It is often the reason this approach is historically viewed as slow and relegated to cold and archival use cases.
These Galois Field based dispersal solutions are also impacted by the data leakage phenomenon.
Data leakage means intruders can infer portions of the original data from the individual pieces and gain access to sensitive contents. Even with encryption, data is not always safe if the keys are compromised.
At Phazr.IO, we used building blocks for secure satellite communication networks to create storage solutions that are implicitly secure, operationally efficient, and highly available.
Our patented approach eliminates data leakage. Regardless if encryptions are applied to data before or after dispersal, your data is always protected. Some of our users even called this "keyless encryption".
We used telecommunication coding techniques to reduce the computational requirement for encoding and decoding data. We can process twice as much data per cycle as the industry state of art implementations.
The Phazr.IO storage technologies allows all users of storage to break out of the boxes set by the limitations of old school methods. This applies to consumers with a smart phone, enterprises deploying private and hybrid storage, and developers creating the next greatest thing.